Acunetix: an XSS Scanner and Much More
Despite being around for 20 years, Cross-site Scripting (XSS) remains the most common web application vulnerability in the world according to many sources, for example, the latest Trustwave report and the HackerOne bug bounty program. With a well-designed Cross-site Scripting attack, an attacker can steal a user session, personal data, modify how an application appears in the victim’s browser, send data as a compromised user, or cause the target to download malware. To protect your business and your users as well as maintain regulatory compliance, you need a web vulnerability scanner that reliably identifies all types of XSS vulnerabilities.
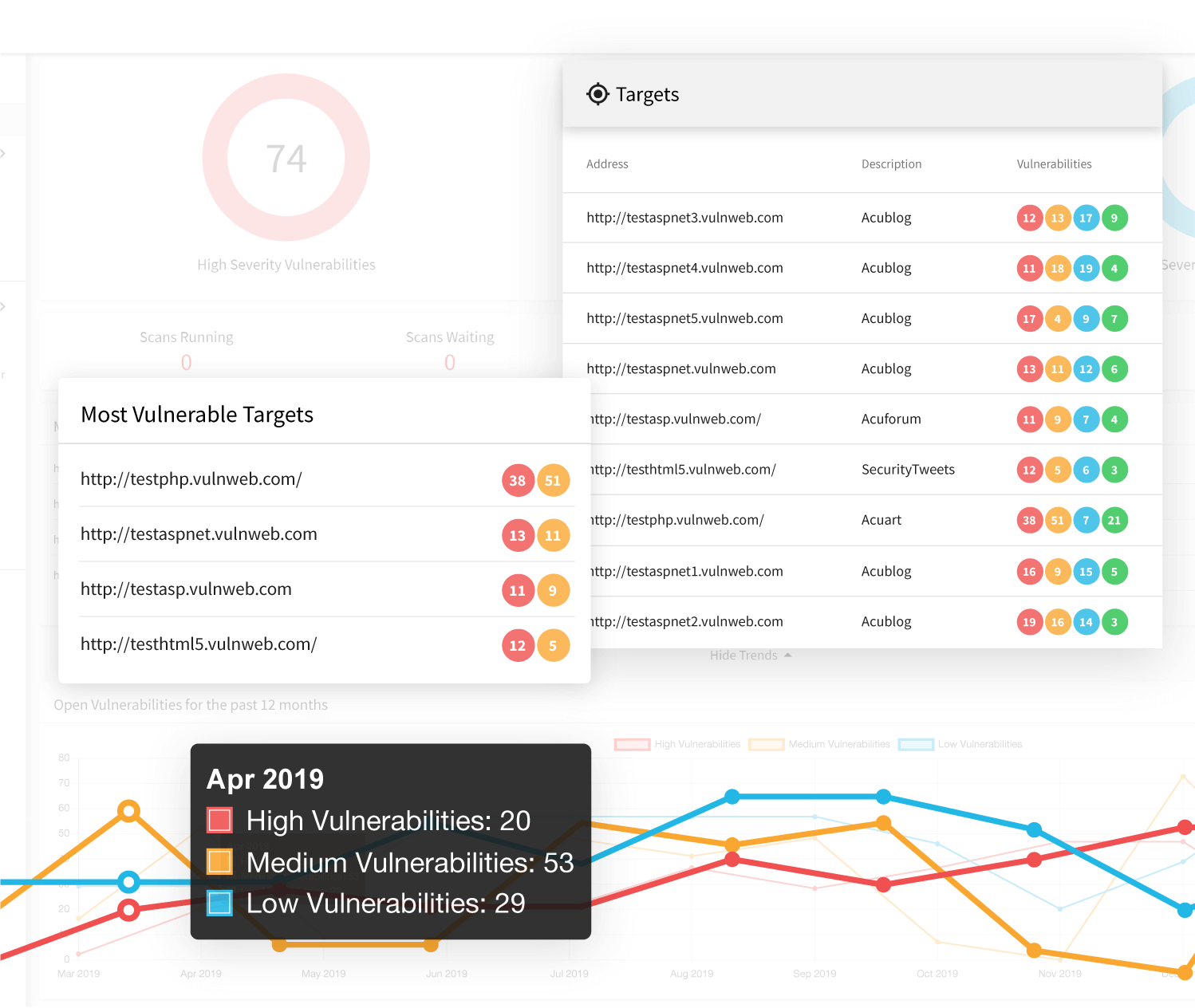
Find All Common Types of Cross-site Scripting Vulnerabilities
Acunetix identifies all common types of XSS vulnerabilities, including those difficult to discover with other security tools. You also get a detailed explanation of every discovered vulnerability and recommendations on how to fix it.
- Acunetix finds stored XSS (also called persistent XSS), including blind XSS. In the case of a stored XSS, the attacker can cause the web application to save a malicious script, which is then served back to victims when they visit the site, often using a different web page.
- Acunetix finds reflected XSS (also called non-persistent XSS). In the case of a reflected XSS, sites return malicious JavaScript code within an HTTP response. Typically, these attacks require minimal user interaction, such as clicking on a malicious link in a phishing email.
- Acunetix also has advanced XSS detection functionality to find DOM-based XSS vulnerabilities. A DOM XSS attack is possible if the web application writes data to the Document Object Model without proper sanitization.
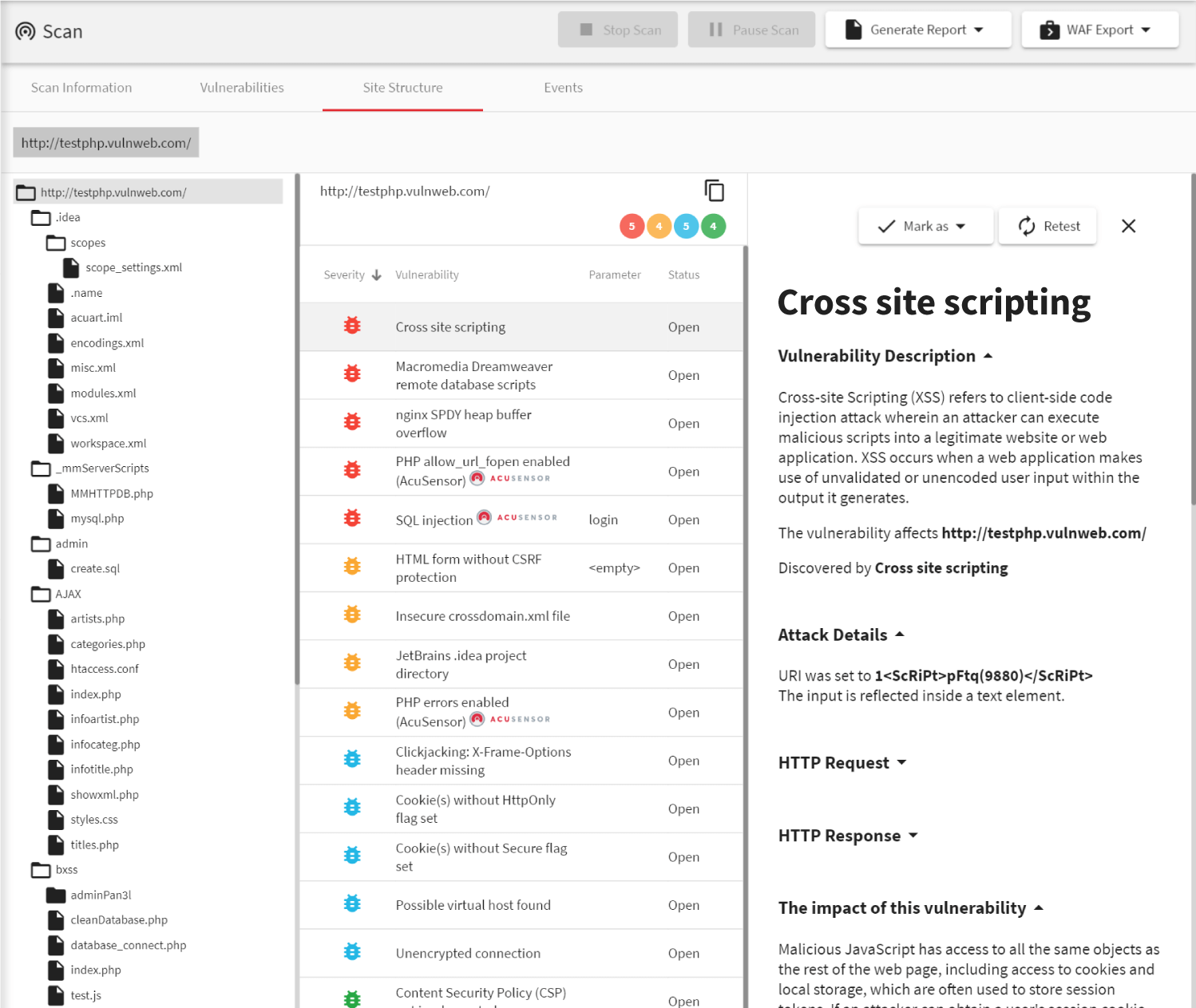
Full-Featured Web Application Security Testing Tool
Acunetix finds not only XSS vulnerabilities but also other types of client-side and server-side web vulnerabilities. It is renowned for its performance and a very low number of false positives. You can use it as the initial penetration testing tool.
- The DeepScan crawler technology lets you identify vulnerabilities in any type of web application. That includes common open-source platforms like WordPress, off-the-shelf commercial applications, or applications uniquely built for your business. Because Acunetix is a black-box (DAST) scanner and does not require access to the source code, it does not matter whether the application is built using PHP, Ruby, Python, or any other server-side language.
- Acunetix finds all web application vulnerabilities, including those in the OWASP Top 10. This includes SQL Injection, cross-site request forgery (CSRF), remote file inclusion, local file inclusion, path traversal, SSL misconfigurations, and more.
- You can also use Acunetix as a network security scanner. Acunetix is integrated with the OpenVAS scanner and can manage network vulnerabilities and web vulnerabilities together.

Enterprise-Class Vulnerability Assessment and Vulnerability Management
In addition to being a leading-edge web security scanner, Acunetix is also a complete vulnerability assessment and vulnerability management solution. The platform automatically assigns priorities to vulnerabilities based on their severity as well as helps you manage the entire remediation process from discovery to final verification.
- You can integrate Acunetix with many popular issue trackers such as Jira, GitHub, GitLab, Mantis, Bugzilla, Microsoft TFS, and more. Acunetix automatically sends newly discovered vulnerability information to issue trackers, creates issues, and assigns them to the right person.
- You can also integrate Acunetix with CI/CD tools such as Jenkins. Your DevOps/DevSecOps/SecDevOps pipeline can include Acunetix scans so that your in-house software is secured as early as possible, saving you a lot of time and resources.
- Acunetix works with many other tools including web application firewalls (WAF), Selenium, and more. In the case of enterprise customers, Acunetix can include custom API integrations that fit the needs and the environment.
Frequently asked questions
Professional vulnerability scanners such as Acunetix can find 99 percent of XSS vulnerabilities but there is always a possibility of new rare attack vectors that can only be found through penetration testing. However, during external benchmark tests, Acunetix discovered 100 percent of Cross-site Scripting vulnerabilities.
Most vulnerability scanners cannot find advanced XSS vulnerabilities such as DOM-based XSS and blind XSS. Acunetix is able to detect DOM-based XSS using a built-in DeepScan engine module. To detect out-of-band vulnerabilities such as blind XSS, Acunetix uses the built-in AcuMonitor technology.
Read more about detecting blind Cross-site Scripting with AcuMonitor.
Acunetix is found to be one of the most effective XSS scanners on the market. It is so effective that independent security researchers use it everyday to find Cross-site Scripting vulnerabilities in external websites and web applications designed by giants such as Google.
Read about how Russian researchers used Acunetix to find XSS vulnerabilities in Google.
The best way to prevent Cross-site Scripting is to apply various forms of encoding to user input, for example, URL encoding, HTML encoding, JavaScript encoding, and more. However, in some cases, input filtering may also be required.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox