Every automated web vulnerability scanner is prone to some false positives and if anyone states otherwise, it is misleading. However, if the scanner uses advanced techniques, certain web vulnerabilities may be discovered with absolute certainty. Acunetix employs several different techniques to reduce false positives. As a result, according to industry benchmarks, Acunetix is one of the leaders in terms of accuracy.
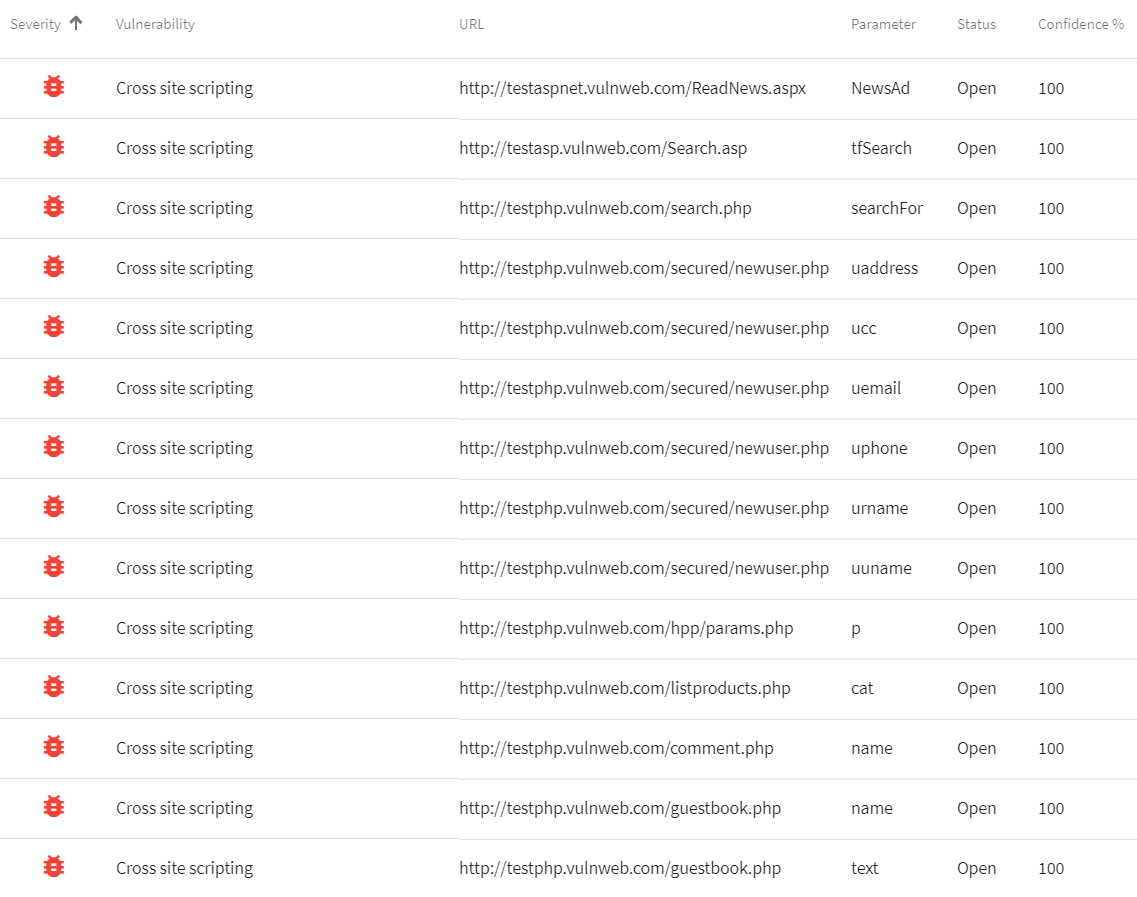
Vulnerability Confidence Levels
The chance of a false positive depends on the type of vulnerability and the technique used to detect it. Acunetix provides three levels of vulnerability confidence, so that you know if you might want to perform further penetration testing.- High confidence vulnerabilities are 100% verified. You do not have to do any further penetration testing for these vulnerabilities. Most vulnerabilities detected by Acunetix are verified.
- Medium confidence vulnerabilities are almost certain but for these types of vulnerabilities, it is simply impossible to provide absolute proof. You may perform further penetration testing if you wish, but in approximately 95% cases, the vulnerability is there.
- Low confidence vulnerabilities are the types of vulnerabilities that cannot be verified automatically but can only be suspected. You may perform further penetration testing, but in the case of these vulnerabilities, we recommend that you directly look at the source code or configuration. From our experience, these vulnerabilities are there in more than 90% of cases.
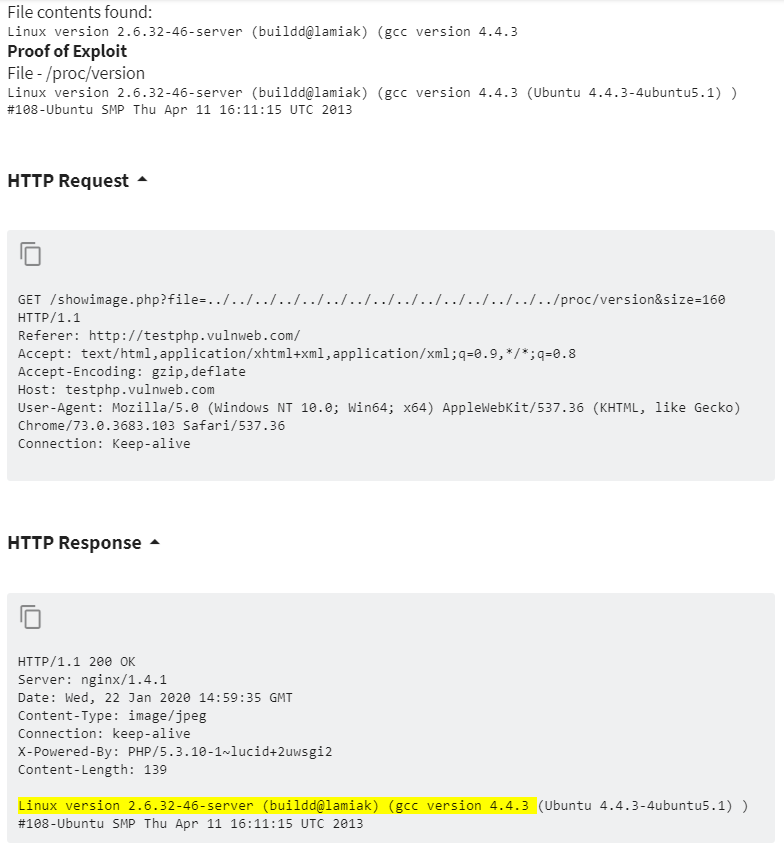
Proof of Exploit
For many critical vulnerabilities, Acunetix goes even further than confirming. The scanner can also provide you with absolute proof that the vulnerability exists. This information is called proof of exploit.- In most cases, the proof is simply a piece of information that should not be available to the user. For example, the administrator account name or a confidential file from the back-end such as a server configuration file. Acunetix uses the verified vulnerability to access such information and displays it in the report.
- The proof is available only for certain vulnerabilities because not every type of vulnerability can be proven by a scanner. For example, most Cross-site Scripting (XSS) vulnerabilities cannot be proven because they affect the client (user’s browser) not the server (your resources).
- Even if no direct proof is available, Acunetix always displays the HTTP request, including the exact payload, and highlights the part in the response used to verify the vulnerability. You can copy and manually send this payload to your server to perform additional verifications.
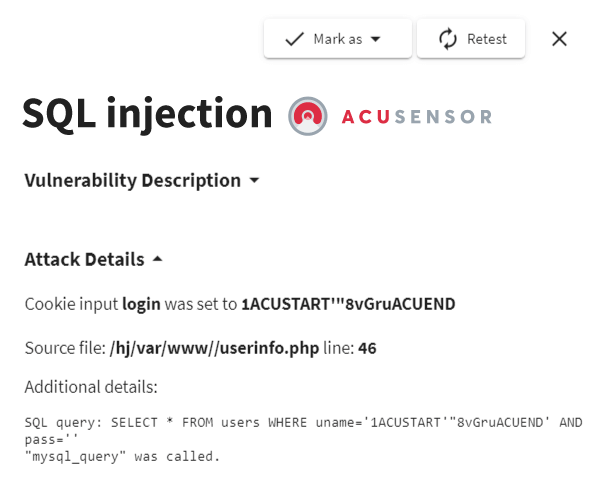
AcuMonitor and AcuSensor Advantages
Acunetix uses additional technologies that not only expand the range of vulnerabilities detected but also increase the confidence with which vulnerabilities are detected.- AcuMonitor is an external service that works with the Acunetix scanner. In the case of certain vulnerabilities, AcuMonitor receives a request as a result of a scanner payload. If so, the vulnerability is 100% proven and cannot be a false positive.
- AcuSensor is an optional component that turns Acunetix into an IAST scanner. Acunetix with AcuSensor can confirm more vulnerabilities because it can monitor the back-end processes, too. For example, it can monitor the SQL query that is executed as a result of an SQL Injection payload, thus being able to prove the vulnerability.
- Additionally, Acunetix security researchers and engineers continuously review and improve algorithms used for vulnerability testing and eliminate false positives as much as possible.
Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox