One of the key features that Acunetix has always focused on is high performance. We know that scanning large applications requires a lot of time. We designed Acunetix and keep improving it so that your scans take as little time as possible and deliver results as early as possible.

Written in C++
The Acunetix engine is written in C++. C++ is a low-level programming language, which means that its compiled code is converted to machine code, making it easier for computer hardware to understand. This makes it very fast and this is why we chose C++ to develop the Acunetix engine. High-level languages such as Java or C#, which are used to develop most applications, are easier for programmers. However, code from these languages is compiled into an intermediary language, which the computer must translate into something that the hardware understands, and this occurs during application execution. As a result, program execution is much slower. Additionally, the Acunetix scanning engine is designed so that it minimizes the number of requests required to test for vulnerabilities. This further speeds up the engine by reducing the potential negative impact of network bandwidth and server load capabilities.Concurrent Crawling and Scanning
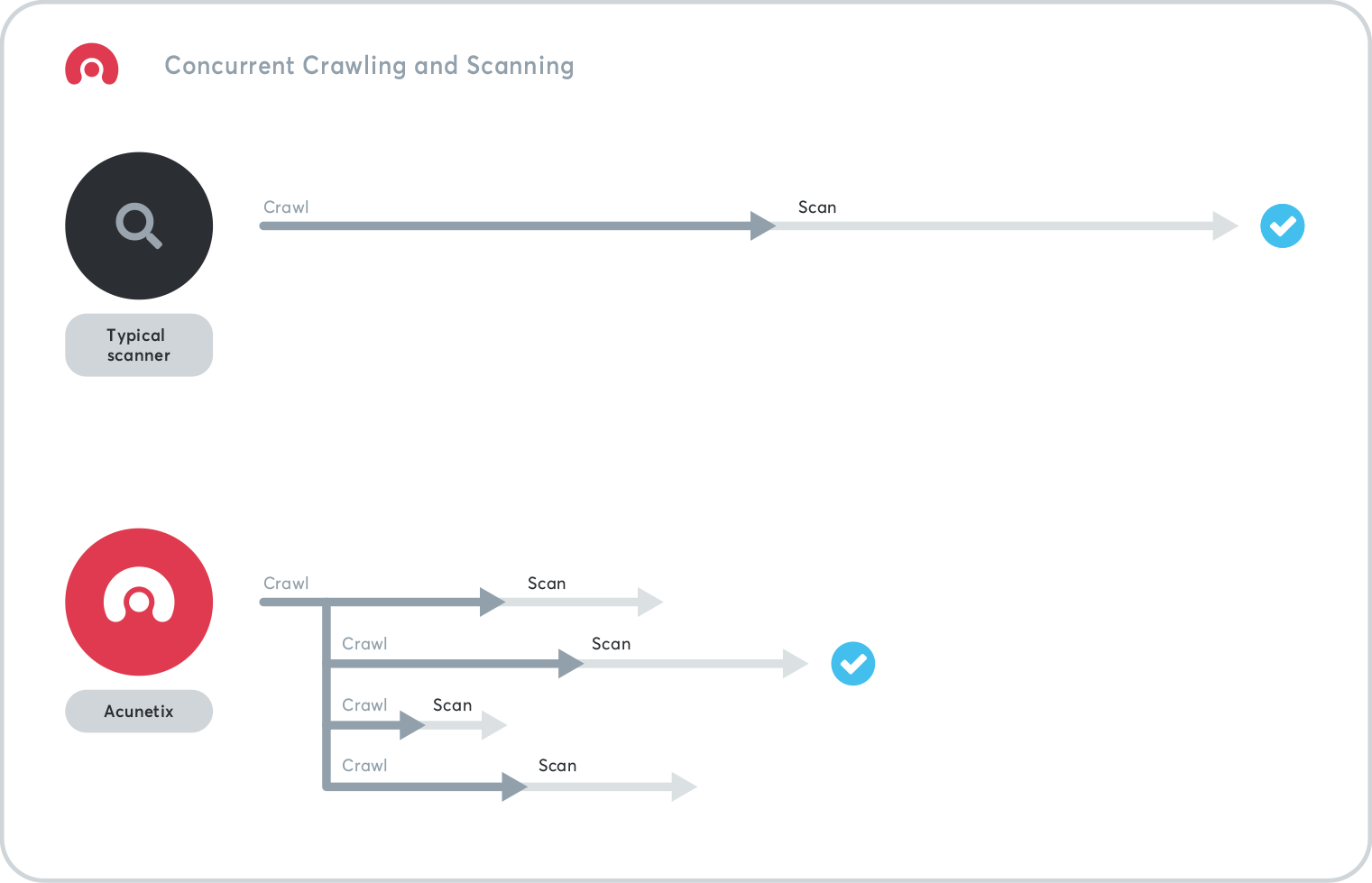
Most web vulnerability scanners work in two phases. First, they crawl the website or web application and determine every possible entry point. After this is completed, they start scanning each page one by one. Acunetix takes a different approach, creating specialized tasks for the scanner. The first task is an initial request to the web application. The response is analyzed and a set of new tasks is created – these can be crawling or scanning tasks. The Acunetix scanner proceeds through the tasks using multiple, dynamically allocated threads to better utilize the machine’s resources.SmartScan Technology
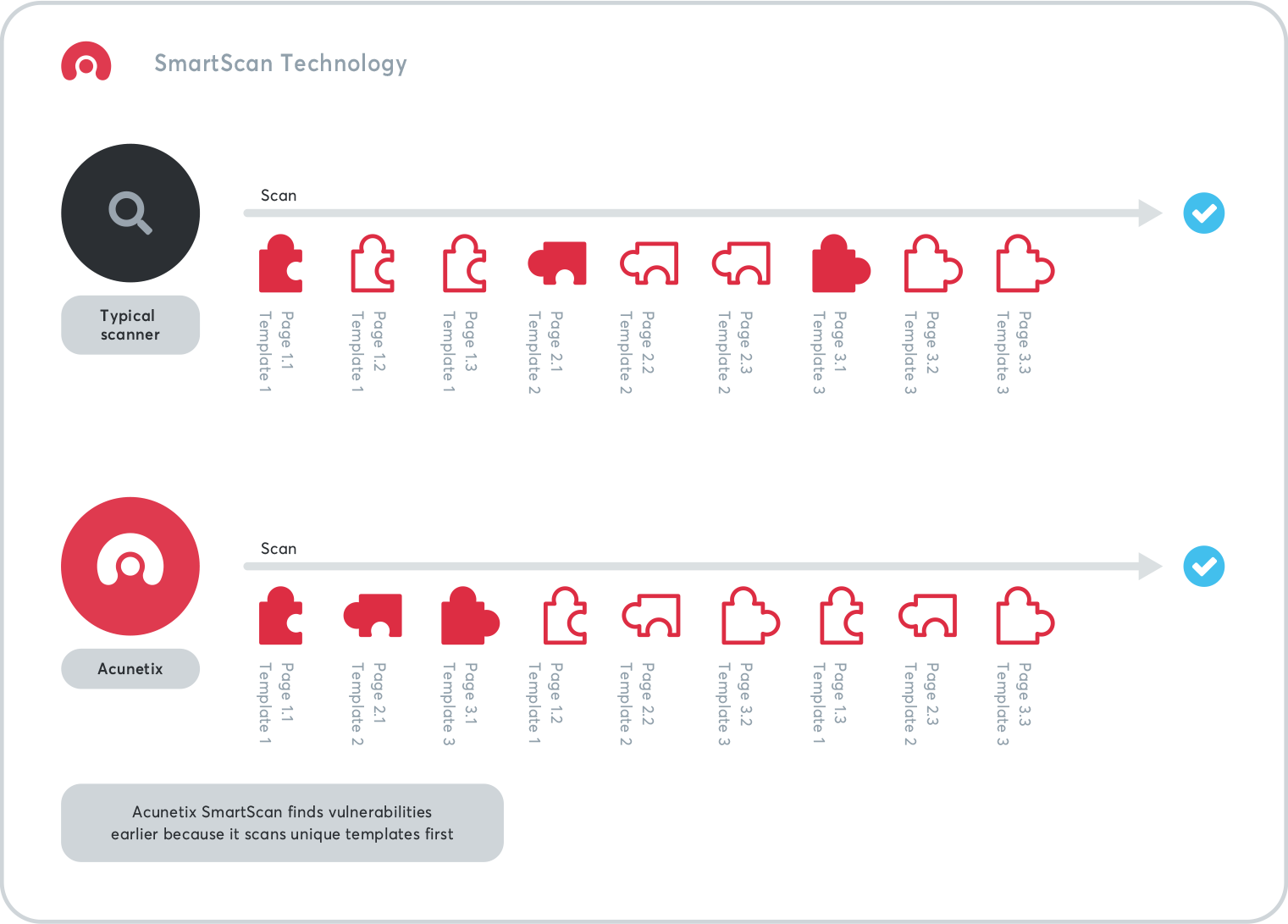
Even with our fastest scanning engine, large web application scans may take many hours. This could be due to network capacity, server capacity and load, and many other factors independent of Acunetix. Therefore, we came up with a technology that helps you get meaningful results as quickly as possible even if your scan is delayed by other factors. The Acunetix SmartScan technology dynamically prioritizes the tasks described above to scan elements on the site, such as pages or forms, which appear dissimilar from elements that have already been scanned. In the case of larger sites, many web pages are based on the same templates and therefore would behave in a similar way even though the content might be different. A crawler often queues these pages for scanning one after another. However, if you scan many pages based on the same template, you usually don’t find any new vulnerabilities. Instead, Acunetix recognizes pages that are similar to those already scanned and pushes them to the back of the queue. This way, the first pages that are scanned are all unique. Depending on the site being scanned, this can mean that you can get up to 80% of the vulnerabilities discovered in the first 20% of the scan.Incremental Scanning
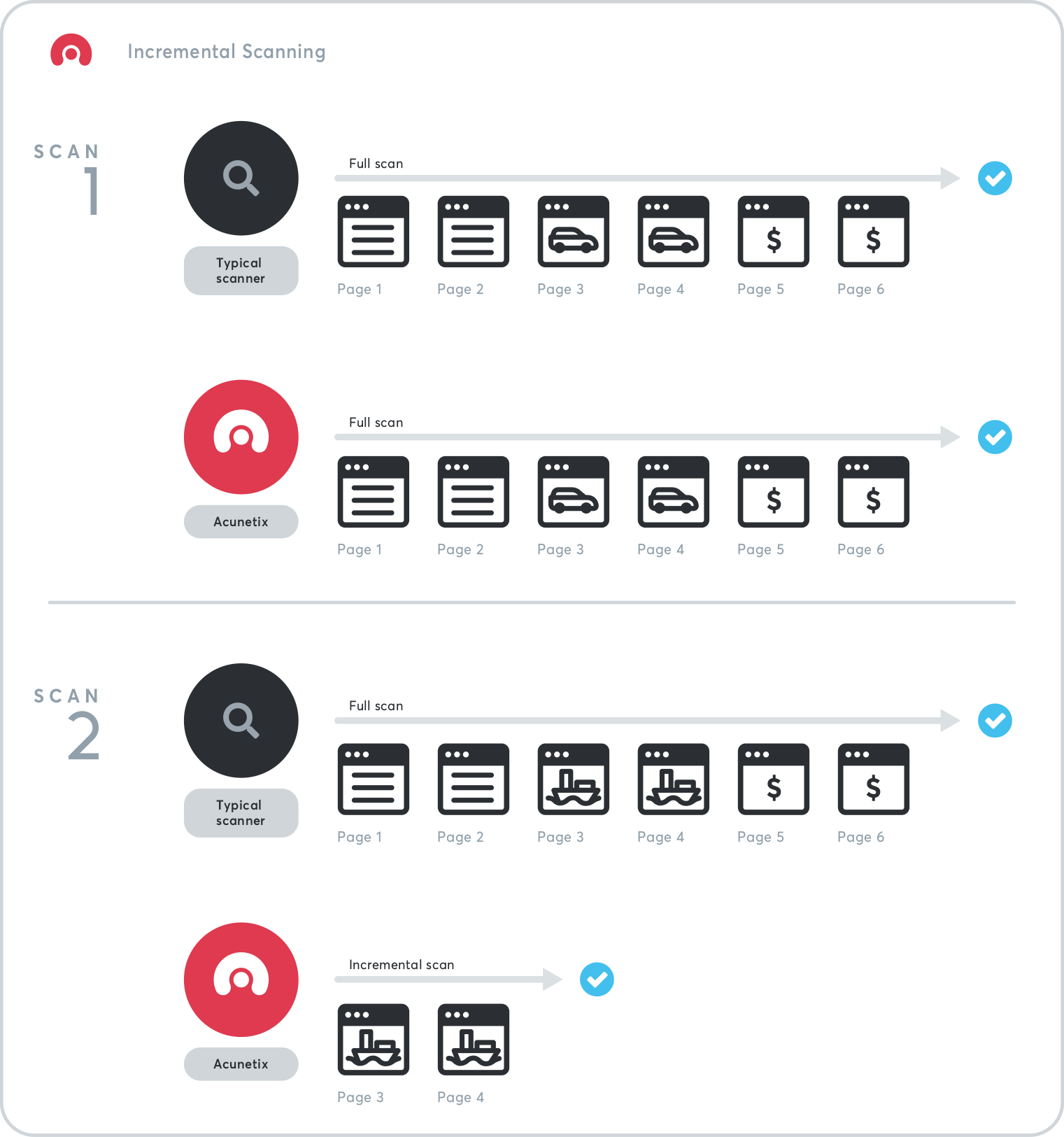
Incremental scans greatly improve performance both for scheduled scanning and for CI/CD build scanning. You may configure Acunetix so that before starting a scan, it compares the previous state of the website or web application with its current state and scans only the elements that changed. For sites that are large and tend to change frequently, we recommend that you perform scheduled scans, enabling the incremental scanning option. If you use incremental scans as scheduled scans or as part of CI/CD pipelines, we recommend that you still perform a full scan before the application is moved to the next development stage.Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox