Web application vulnerabilities are now your external vulnerabilities
Before cloud-based web applications came to dominate business software, most external vulnerability scanning would be limited to the external network infrastructure immediately reachable to attackers and focus on network vulnerabilities. Today, the majority of data breaches originate from attacks on web applications and APIs. In effect, the scanning perimeter has moved from the network to the application layer—with the major difference that when you’re in the cloud, you can’t lock away your entire environment behind a firewall like you could on premises. To keep up with malicious hackers, organizations need to start treating web apps and APIs as their external attack surface and web vulnerability scanners as their external vulnerability scanners. Acunetix is a mature and proven solution for dynamic application security testing (DAST) that can crawl and test the vast majority of modern websites and applications regardless of technology stack, including all-dynamic JavaScript and HTML5 applications. Acunetix also features a fully integrated external network vulnerability scanner based on the open-source OpenVAS, allowing you to rapidly and continuously scan your perimeter for vulnerabilities and misconfigurations both in the application and network layers.Fast, flexible, and continuous external vulnerability scanning
Web development is constantly evolving, with ever-changing technologies being used to build increasingly complex apps. Many external vulnerability scanners and black box scanners can’t fully scan, large and complex web applications because they were designed for a past world of mostly static web pages. Acunetix, on the other hand, was built for accuracy and speed, featuring an integrated browser engine and a highly tuned crawler and scan engine to perform complete external vulnerability scans even on large and complicated applications without breaking a sweat—and without swamping your teams with false positives. For added security and flexibility, you can schedule external vulnerability scans to run at specific times of a day, week, or month, or even define you own custom schedule. You also have the option of running scans on a continuous basis with Acunetix only running a quick scan every day of the week, with a full scan run once a week. This ensures that any new vulnerabilities that may have been introduced in between full scans still get picked up. Additional features such as configurable scan rate limiting help to ensure that you can run external vulnerability scans using Acunetix even on high-traffic sites without affecting their performance.
Clear and actionable vulnerability management and reporting
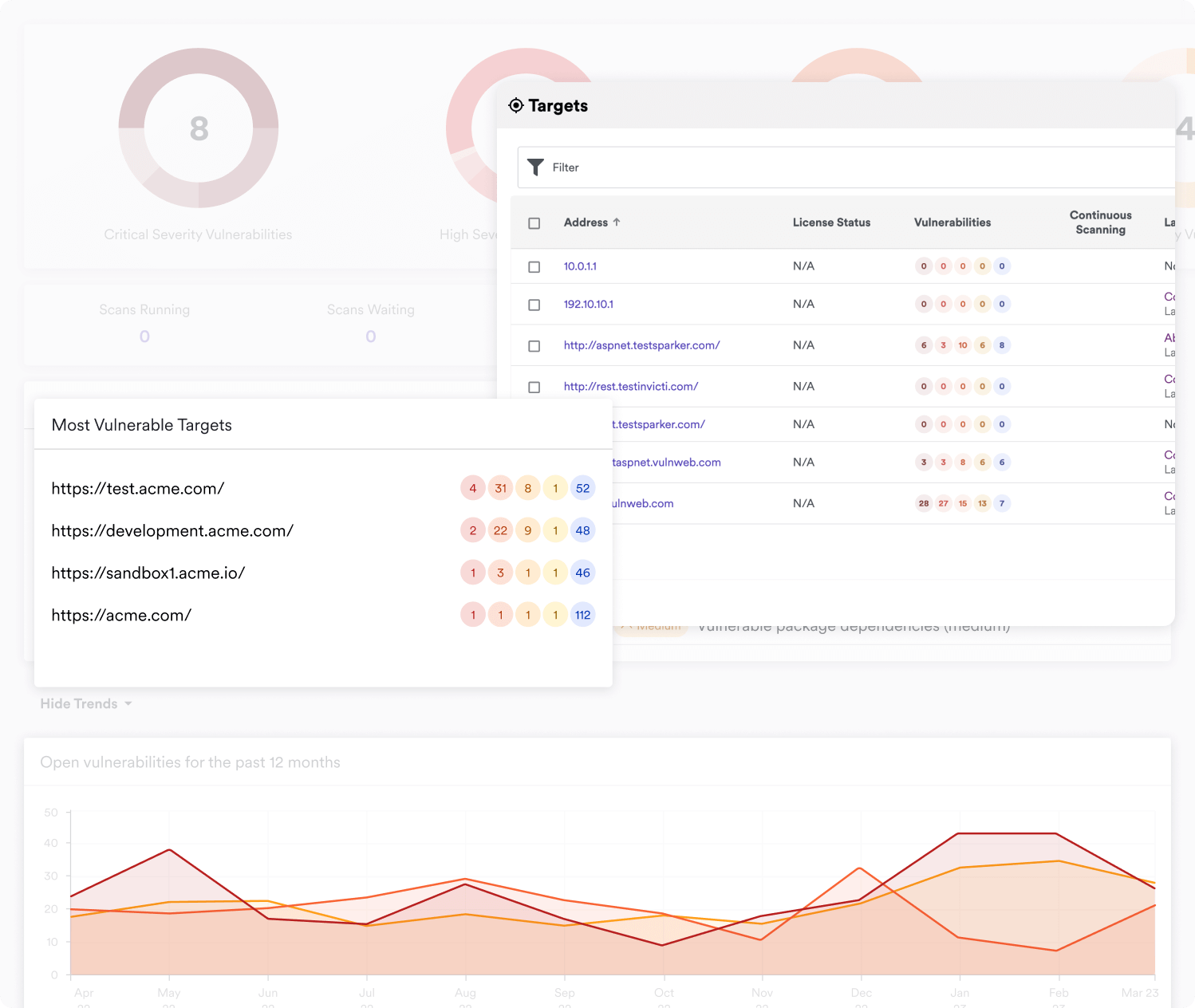
Built-in vulnerability management, prioritization, and reporting features in Acunetix are another major advantage compared to most vulnerability scanning tools, especially tools originally designed for penetration testing. After an external vulnerability scan is complete, Acunetix can instantly generate a wide variety of technical and regulatory and compliance reports such as PCI DSS, HIPAA, OWASP Top 10 and many others. Acunetix also lets you export discovered vulnerabilities to third party issue trackers such as Atlassian Jira, GitHub, GitLab, Microsoft Team Foundation Server (TFS), Bugzilla, or Mantis—and that’s in addition to built-in integrations that let you create tickets directly in supported collaboration tools. One of the biggest issues with conventional external vulnerability scanners is that they simply show a list of scan results. In contrast, Acunetix provides its own vulnerability management functionality, keeping track of open vulnerabilities found during each scan. After a vulnerability is fixed, Acunetix can re-test just the relevant page to make sure the vulnerability is properly fixed and then automatically mark it as resolved. All this information, combining web and network scanning in one place, is available at a glance in the Acunetix Dashboard. There are even multi-user and multi-role capabilities to make sure each user can only see what they’re meant to.Frequently asked questions
An external vulnerability scan, also called a perimeter scan, is a type of vulnerability scan that is performed from outside the host or network. Such a scan emulates the behavior of a potential external attacker. It focuses on finding security vulnerabilities in assets that are exposed by design and also on finding assets or information that should not be exposed externally.
Network and web cyberattacks can be performed both externally and internally. However, most companies are more worried about external attacks by cybercriminals than insider risks, treating external vulnerability scanning as more important. However, internal assets must also be secured because they are often used for privilege escalation.
Read how an external SQL Injection attack may lead to internal system compromise.
In the case of web vulnerability scanning, you can expose internal assets to an external web vulnerability scanner. In the case of network scanning, it is more difficult because the purpose of a network scanner is to check for open ports and service exposure. Therefore, it is more effective to use an on-premises scanner for internal network scans.
Learn how to configure Acunetix to scan internal web assets.
With Acunetix Online and Acunetix on-premises, you can perform web vulnerability scans and network scans, both external and internal. In Acunetix Online, network scanning is ready to use as soon as you log in. In the case of Acunetix on-premises, you need to separately install OpenVAS and provide its listening address and port to Acunetix.
Learn how to enable network scanning in Acunetix on-premises.
Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox