There’s no denying the role that JavaScript has played in making web applications the sleek, interactive, online experiences that we know and love today. This powerful scripting language brought interactivity and animation to the web. But with great power comes great responsibility. Cross-site Scripting (XSS) remains a persistent stalwart among the OWASP Top 10. Malicious JavaScript code injected into the DOM is all it takes to compromise a user’s data and avoid conventional, server-side centered XSS vulnerability scanning techniques. Let’s take a closer look at DOM-based Cross-site Scripting (XSS) vulnerabilities and how the Acunetix DeepScan technology can help you prevent a hack.
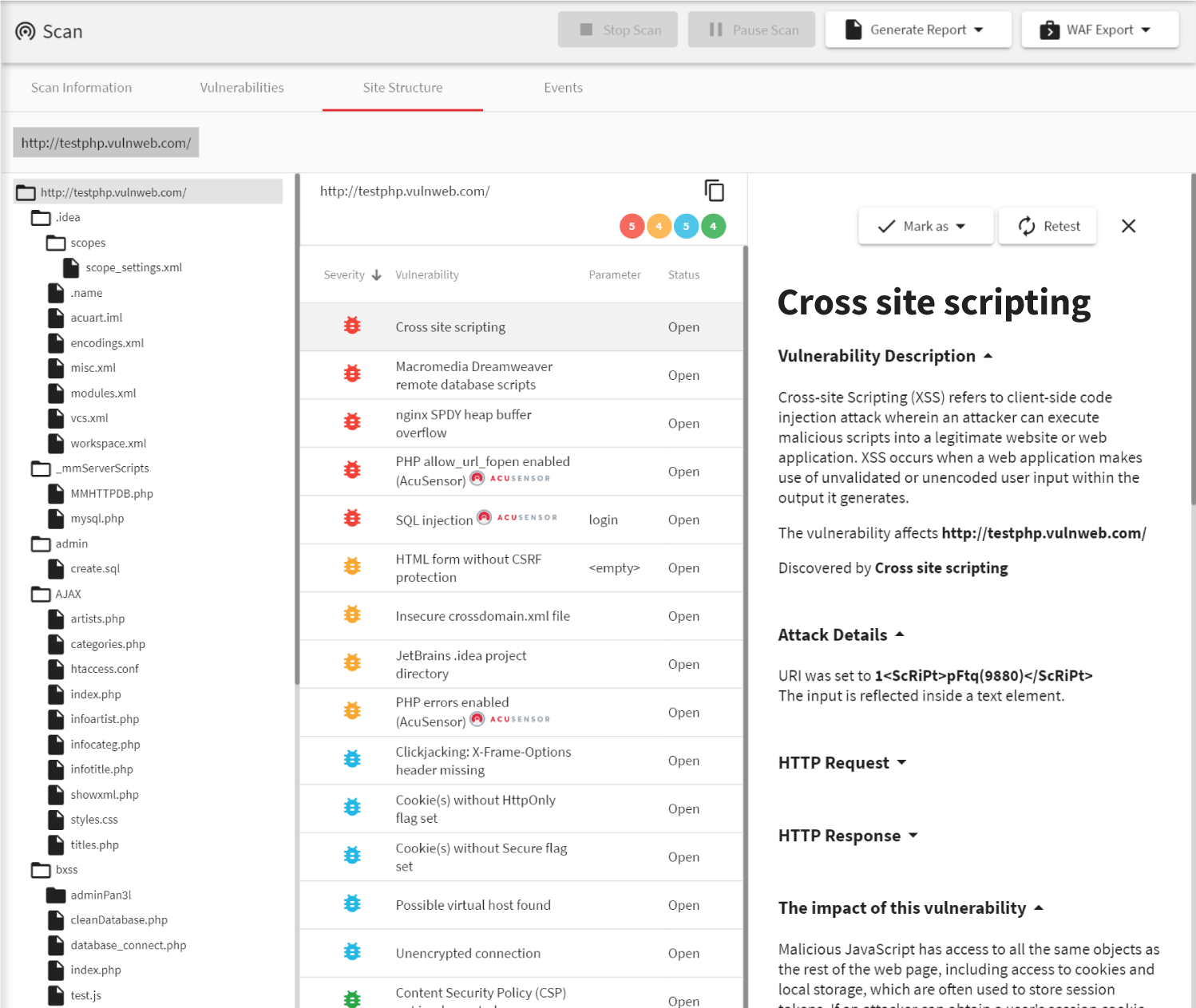
What is DOM-based XSS?
The Document Object Model (DOM) lets web developers dictate through HTML source code how a user’s web browser should display a web page. DOM-based XSS attacks seek to exploit the DOM in a simple two-step process:- Create a Source: Inject a malicious script into a property found to be suceptible to DOM-based XSS attacks. Common injection vectors include document.url, document.location, and document.referrer objects.
- Exploit the Sink: A sink is the point in the data flow where the browser will execute the malicious JavaScript code hidden in the DOM. Common sinks include document.write, setTimeout, and setInterval.
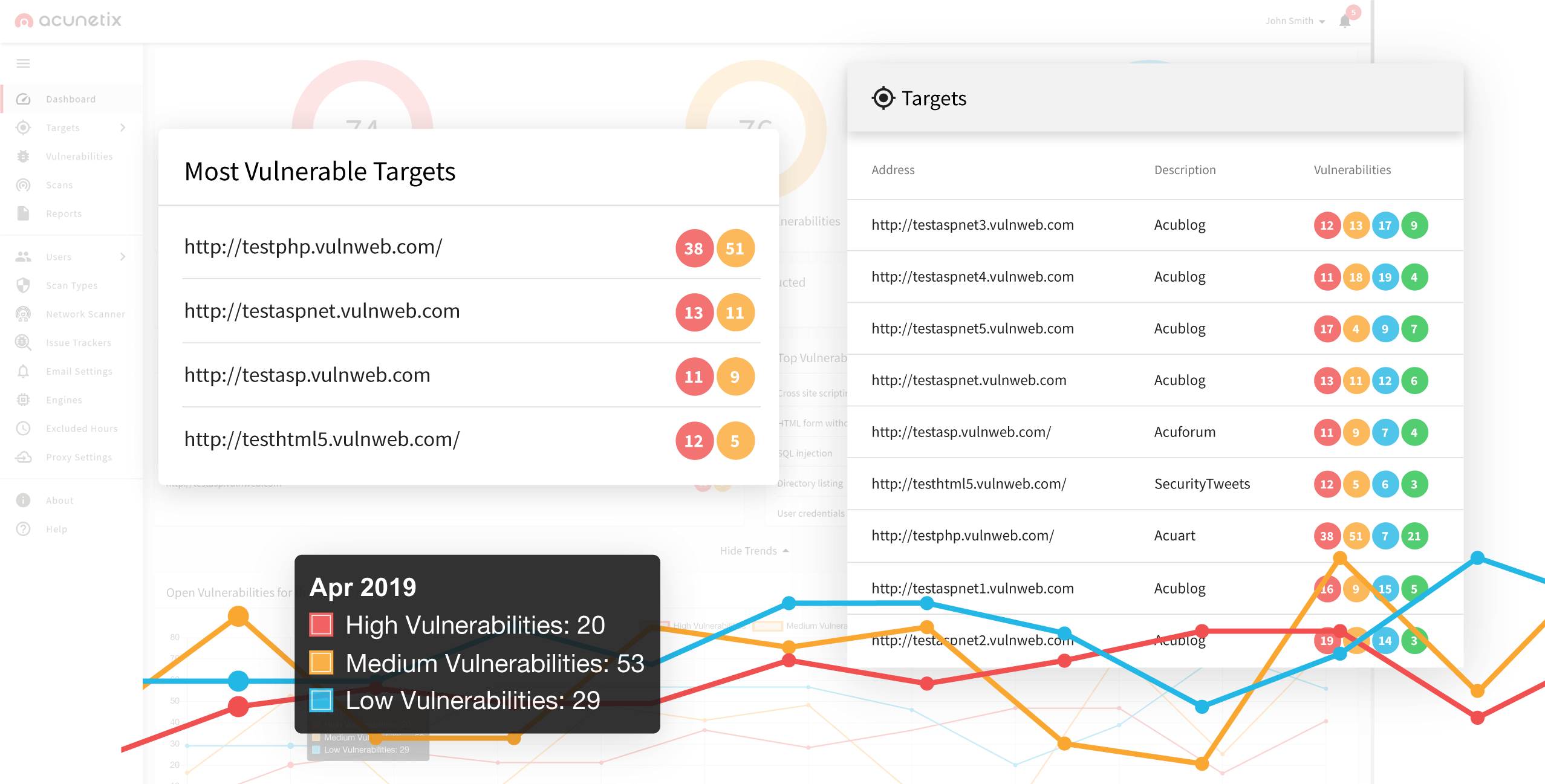
DOM-based XSS Scanner
In order to find the source of a DOM-based XSS vulnerability before the hackers do, you’ll want to scan the client side of your web application with a DOM XSS scanner. The Acunetix Web Vulnerability Scanner contains all the tools you’ll need to sniff out DOM XSS sources. With the highest SQLi and XSS detection rate in the industry, Acunetix can crawl your web application and without fear of false positives.Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox