MANAGE YOUR WEB AND NETWORK SECURITY TOGETHER USING
Acunetix Network Vulnerability Scanner
Network Vulnerability Scanner: Enter Acunetix!
Network security issues are still the cause of many data breaches. This makes perimeter network vulnerability scanning, one of the baseline vulnerability assessment exercises any organization should routinely subject themselves to. Perimeter network vulnerability tests help make sure that no network devices, web servers or other public-facing network assets are susceptible to trivially exploitable vulnerabilities.

Scan Perimeter Network Services
Acunetix Premium features deep integration with the widely popular open-source OpenVAS network security scanner. Apart from being a baseline security analyzer, Acunetix can be used to run comprehensive perimeter network security scans that will look for over 50,000 known network vulnerabilities in everything from network devices, web servers, and operating systems. Moreover, Acunetix seamlessly integrates network security findings with web application vulnerability scan results in a single web-based GUI, making it a one-stop-shop for information security professionals tasked with performing external security testing – be that on bare metal infrastructures, as well as public or private clouds. What’s more, in Acunetix it’s possible to schedule scans to run at specific times of a day, week or month, or even define your own custom schedule. Additionally, you also have the option of running scans on a continuous basis with Acunetix only running a quick scan every day of the week, with a full scan run once a week. This ensures that any new vulnerabilities and configuration issues that may have been introduced in-between full scans get picked up by Acunetix immediately.
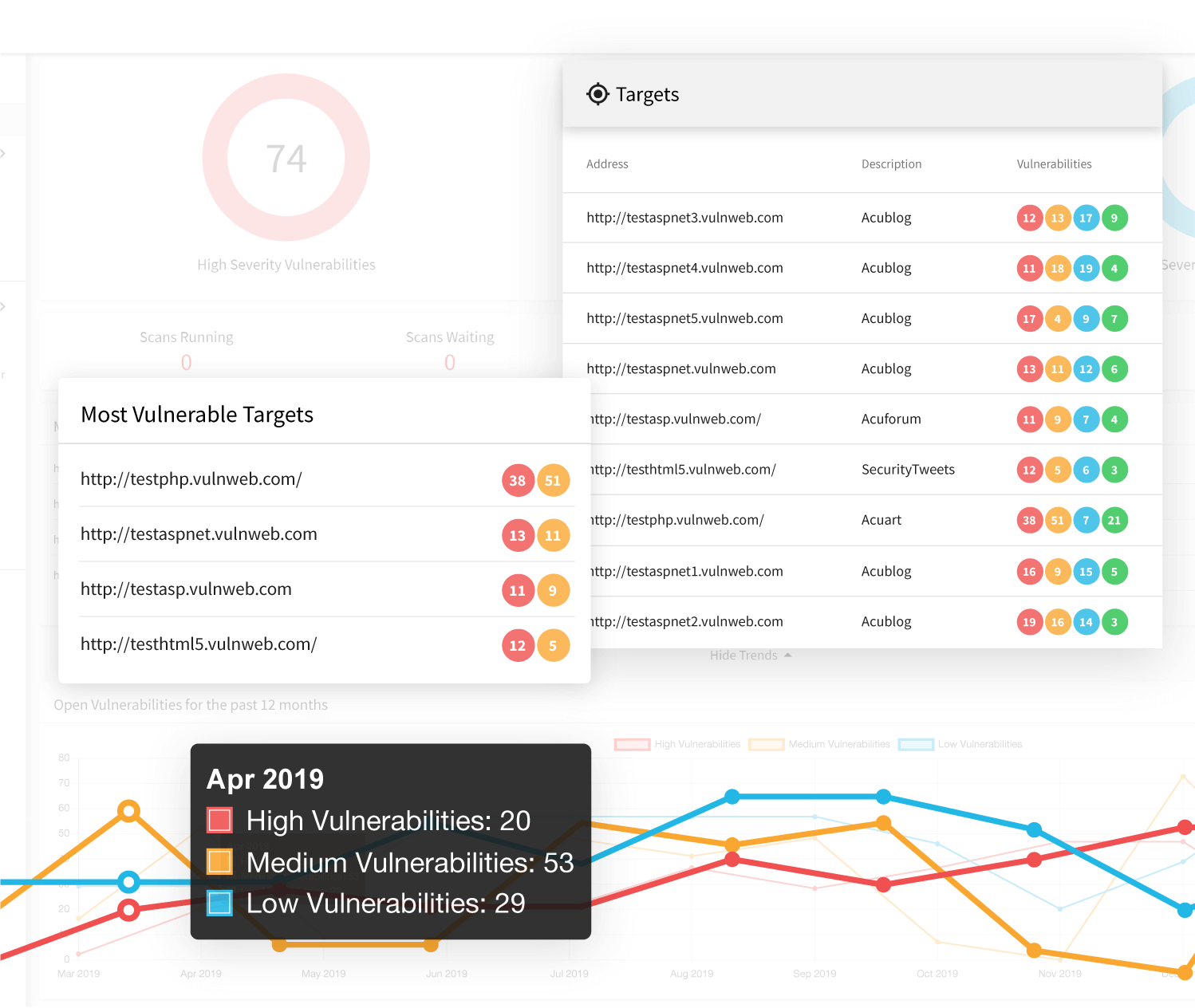
Keep on Top of Your Network Vulnerabilities
Another area in which Acunetix’s network scanning tool excels in over other security tools is the ability to produce great reports. After a scan is complete, Acunetix can instantly generate a wide variety of technical and regulatory and compliance reports such as PCI DSS, HIPAA, OWASP Top 10 and many others. Additionally, Acunetix also allows users to export discovered vulnerabilities to issue trackers such as Atlassian JIRA, GitHub, GitLab, Microsoft Team Foundation Server (TFS), Bugzilla, and Mantis. One of the biggest issues with conventional vulnerability scanners is that they simply report a list of vulnerabilities and configuration errors after a scan is complete. Acunetix takes a different approach in that once a vulnerability is found during a scan, it is automatically cataloged and assigned a status of Open. After the vulnerability gets fixed, Acunetix may be used to re-test the vulnerability to make sure it’s properly fixed, and then automatically marks it as Fixed. All of this information is available at a glance in the Acunetix dashboard and thanks to multi-user, multi-role capabilities, users can only see what they’re meant to.
Frequently asked questions
During a network vulnerability scan, an automated network vulnerability scanner checks for potential attacker entry points. Such a tool attempts to identify all network devices on your network and all network services exposed by these devices. Then, it checks if those services expose vulnerabilities, for example, old and vulnerable software versions.
Network vulnerability scanning looks for network services that should not be exposed and vulnerable versions of hardware and software. Web vulnerability scanning looks for vulnerabilities in web services that are exposed by definition and for errors introduced by web developers. The two types of scans are quite different.
Read about the importance of network scanning with Acunetix.
Most businesses are migrating to the cloud so there are fewer network exposure points. Therefore, we believe that network scanning is now less important than web scanning. In the case of web technologies, you need network scanning primarily if you host your own web servers at your premises, not in the cloud. However, to be safe, you should regularly perform both types of scans.
Learn how to use Acunetix Online to scan services that are not exposed publicly.
Acunetix is a specialized web vulnerability scanner, the pioneer of such technology. Network scanning in Acunetix is done with the help of another pioneer and leader, OpenVAS. Therefore, with Acunetix, you get two best-in-genre products working together using a single interface. You cannot get that from competing products, which are network scanners with limited-capability web vulnerability scanning add-ons.
Recommended Reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox