Penetration testing (also called pen testing) is the most efficient way to discover and eliminate real-world potential vulnerabilities that lead to cyber attacks and data breaches. Penetration testing basically means that an ethical hacker performs a simulated attack and attempts to gain access to resources that they should not have access to or perform operations that they should not be able to perform. If successful, the penetration tester explains how it was done so that developers can fix the security vulnerability before a black hat hacker exploits it.
However, penetration testing must be performed by security experts. Security professionals who are skilled enough in ethical hacking to do pen testing are rare and valuable. If pentesters focus on basic security testing, they have no time to discover all security vulnerabilities. That is why automating penetration testing as much as possible is very important – this automation is called vulnerability scanning.
Pen testing is especially important for cybersecurity in the case of web application security because, unlike in the case of network security, web applications are often written, modified, or configured in-house. Here is our view on what is penetration testing and here are some suggestions about how you can use Acunetix as penetration testing software.
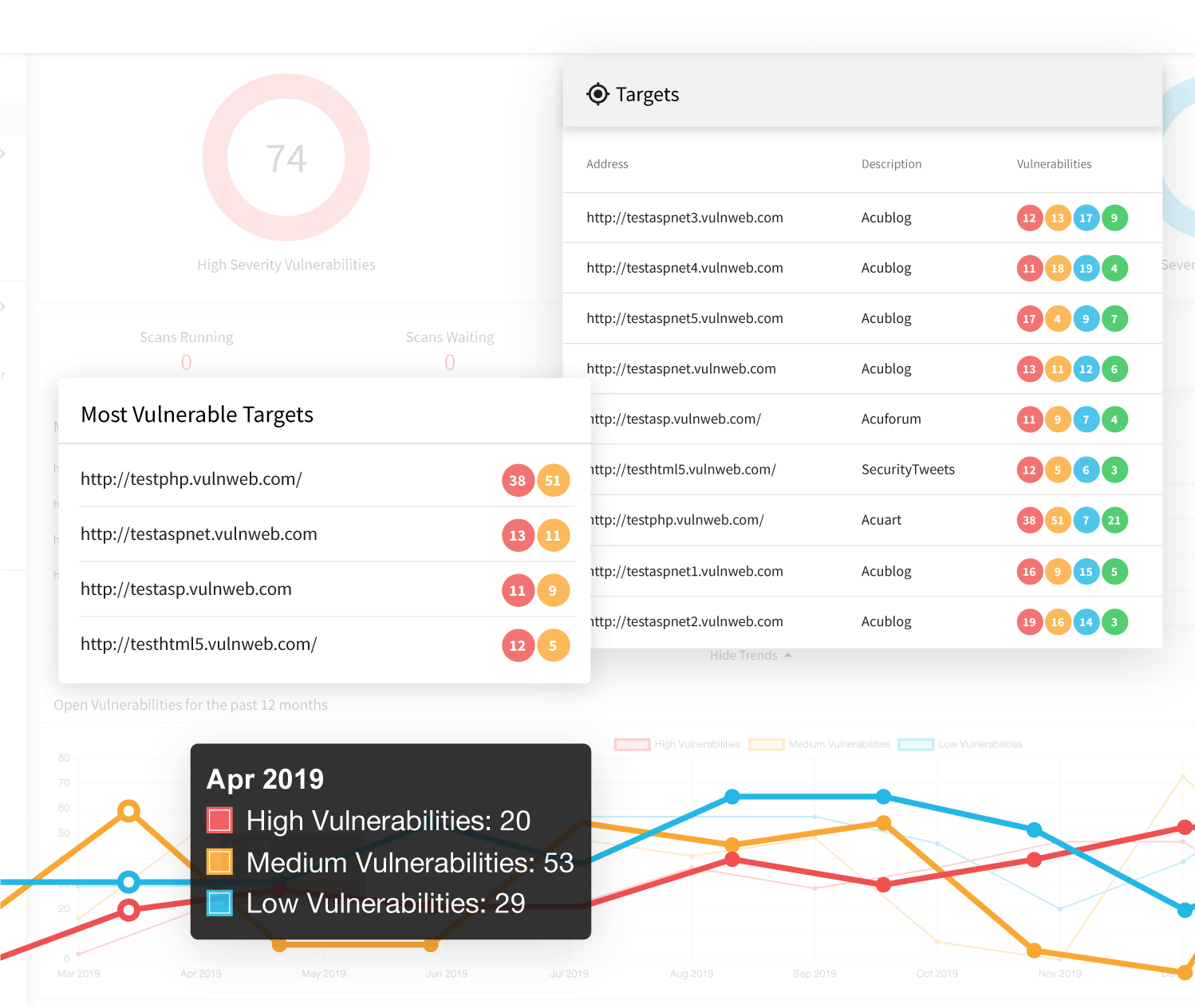
Using Acunetix as an Initial Web Application Penetration Testing Tool
Acunetix is used by security experts and ethical hackers as well as companies offering penetration testing services worldwide. However, it is also used by businesses with limited knowledge about information security. With Acunetix, you can find most vulnerabilities early on so that the security team can focus on the more advanced testing process and finding vulnerabilities that cannot be found automatically, for example, business logic vulnerabilities.- Actunetix automatically finds and proves security issues such as SQL Injections and Cross-site Scripting (XSS). Such security flaws, especially when combined with social engineering and phishing, can let an attacker access your sensitive data or impersonate your users.
- Acunetix not only finds and proves vulnerabilities but also performs vulnerability assessment, evaluating the urgency of the issue and its potential impact on the security posture of your business. The scanner also gives you extensive information on how to fix the vulnerability.
- While spot checks are important, it’s even more important to maintain continuous security and perform regular re-testing. Acunetix offers many security measures for continuous security including incremental scans, new vulnerability scans, and high severity scans.

Integrating Acunetix in the Software Development Lifecycle
If you use ready-made web applications, for example, open-source products like WordPress, your security controls are mostly based on periodic testing. However, if you build any websites or web applications or even modify open-source products, you want to know about dangerous errors as soon as possible. Therefore, your best security policy, in this case, is to integrate automated penetration testing (vulnerability scanning) into your software development lifecycle (SDLC).- If you build web applications, you most probably use some kind of an issue tracking system such as Jira, GitHub, GitLab, BugZilla, etc. You don’t have to manually enter vulnerabilities discovered by Acunetix into such systems. Acunetix creates issues automatically and assigns it to the right person.
- If you use a DevOps approach in your application development, you can use a DevSecOps or SecDevOps approach instead. If you use Jenkins, all you need is to configure the Acunetix plugin for Jenkins and Acunetix will perform black-box testing in real-time as part of your post-build testing methodology.
- Acunetix is a black-box testing tool (DAST), which means that it tests the final application with no access to the source code. This is a more efficient approach than white-box testing (SAST), which needs access to the source code and works only with selected languages. However, with AcuSensor, you can get the best of both worlds in one security tool and implement grey-box testing (IAST).
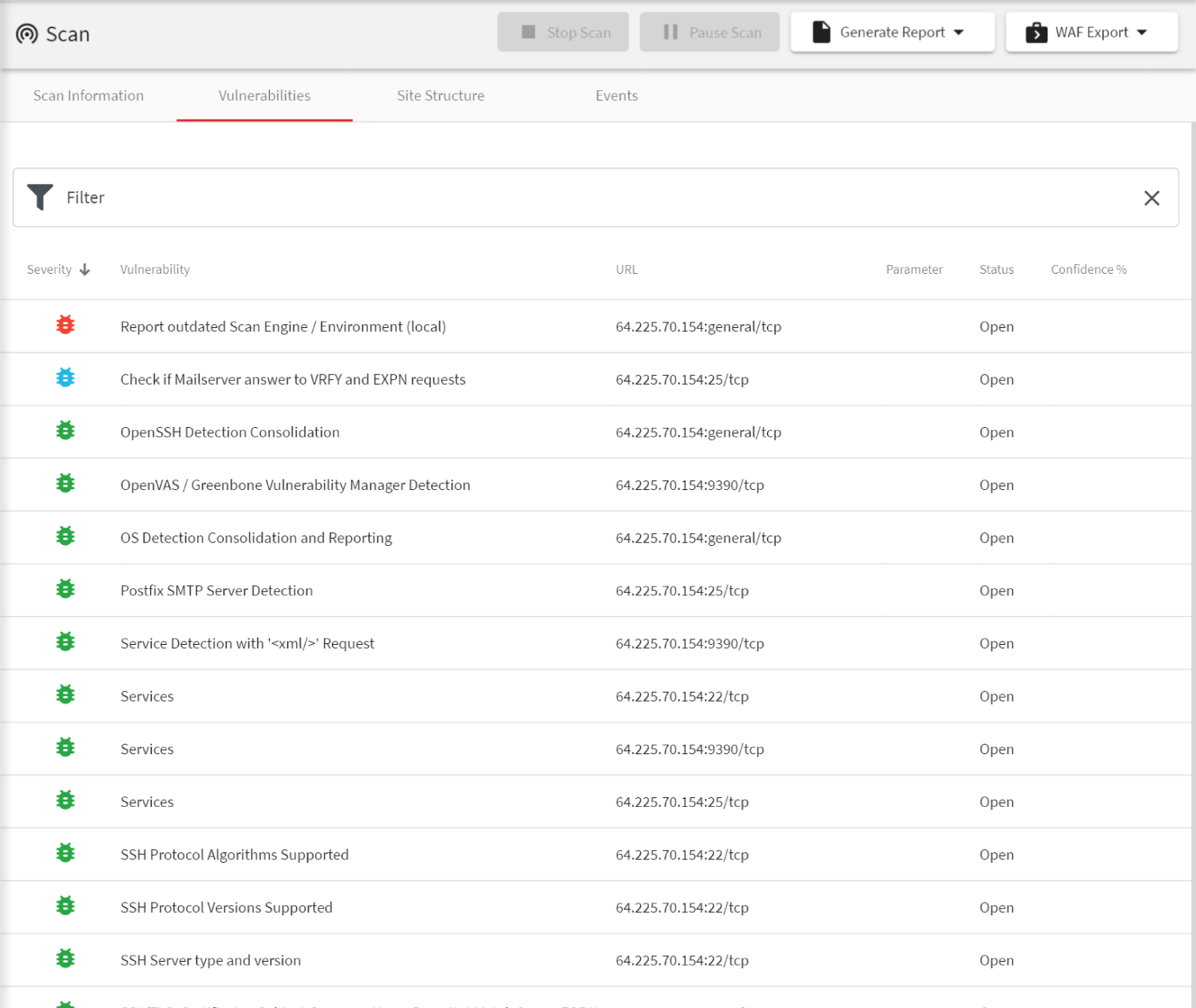
Network Penetration Testing and Beyond with Acunetix
Web application security is much more important today than network security. Most businesses have small local computer system networks and their critical assets are in the cloud. However, in some cases, network penetration testing still needs to be part of the security program. This is where Acunetix shines and offers more than anyone else.- Acunetix is integrated with the world’s most popular open-source network security scanner, OpenVAS. Full integration means that you see all automated penetration testing results in the same Acunetix interface and you can use powerful features of Acunetix for network issues as well (for example, integration).
- In addition to web application security and network security, Acunetix also tests your websites and web applications for malware that could be present on the web server. Acunetix does this by utilizing anti-malware software present in your operating system: Windows Defender on Windows or ClamAV on Linux and macOS.
- If you discover any issues with Acunetix but are short on resources, Acunetix lets you automatically export rules to web application firewalls (WAFs): Imperva SecureSphere, F5 BIG-IP Application Security Manager, Fortinet FortiWeb, or Citrix WAF. This way, you can temporarily band-aid the problem until your developer can fix it.
Recommended reading
Learn more about prominent vulnerabilities, keep up with recent product updates, and catch the latest news from Acunetix.

“We use Acunetix as part of our Security in the SDLC and to test code in DEV and SIT before being promoted to Production.”
Kurt Zanzi, Xerox CA-MMIS Information Securtiy Office, Xerox